CoDeKu DevOps Academy Blog - DevOps & Cloud Blogging Platform
In today’s digital world, where cybersecurity, data governance, and seamless IT operations are non-negotiable, Active Directory (AD) stands as the unsung hero of enterprise networks.
Active Directory is the invisible force that authenticates you when you log in, decides which folders you can access, and ensures that policies are enforced across thousands of devices—quietly and efficiently.
But how exactly does it work, and why is it so vital to the health of a modern IT ecosystem? Let’s dive deep and break it all down in plain English.
📑 Table of Contents
- ❖ What is Active Directory?
- ❖ Active Directory Domain Services (AD DS)
- ❖ Understanding the Structure of AD
- ❖ How Active Directory Works Behind the Scenes
- ❖ Key Concepts in Active Directory
- ❖ Sites and Global Catalog Servers
- ❖ Why AD Management and Security is Important
- ❖ Benefits of Active Directory
🌐 What Is Active Directory?
At its core, Active Directory is Microsoft’s centralized directory service that manages users, computers, and other resources in a network. Introduced with Windows 2000, AD has since evolved into a powerhouse that enables organizations to control access, secure data, and enforce policies across their entire infrastructure.
Think of it as the brain of the network—a system that decides:
- Who you are,
- What you’re allowed to access,
- And how your environment should behave.
🧠 The Building Blocks: AD Domain Services (AD DS)
Active Directory is powered by a service called Active Directory Domain Services (AD DS). This service manages:
- User identities and passwords
- Computer and server access
- Group policies and security controls
It’s where all the magic happens—from validating your login credentials to deciding whether you can install that app on your work computer.
AD DS isn’t a standalone feature; it’s hosted on a Domain Controller (DC)—a Windows Server that serves as the central repository of all directory information.
🏗️ Understanding the Structure of AD
Active Directory isn’t just a flat list of users—it’s a hierarchical system built to scale with your organization.
🔹 1. Forest
A forest is the topmost container. It can include multiple trees and provides the security boundary for everything inside it. Think of it as a secure ecosystem where all domains follow the same rules.
🔹 2. Tree
Inside each forest is at least one tree, a group of domains that share a continuous namespace (like example.com, sales.example.com). Trees allow structured, scalable domain design.
🔹 3. Domain
A domain is the heart of AD. It contains all the users, computers, and resources under one logical boundary. Each domain has its own policies and permissions and is managed by one or more Domain Controllers.
🔹 4. Organizational Units (OUs)
OUs are like folders within a domain. They help administrators organize and manage users, computers, and policies based on real-world structures—departments, locations, or roles.
🔹 5. Group Policies
These are rulebooks applied at the OU, domain, or site level. Want to disable USB access on all marketing computers? Group Policies make it possible—with a few clicks and zero manual effort.
🧠 How Active Directory Functions in Practice
While the structure of Active Directory (with forests, domains, and OUs) defines how it’s organized, the real power of AD lies in how it operates and stores information across the network.
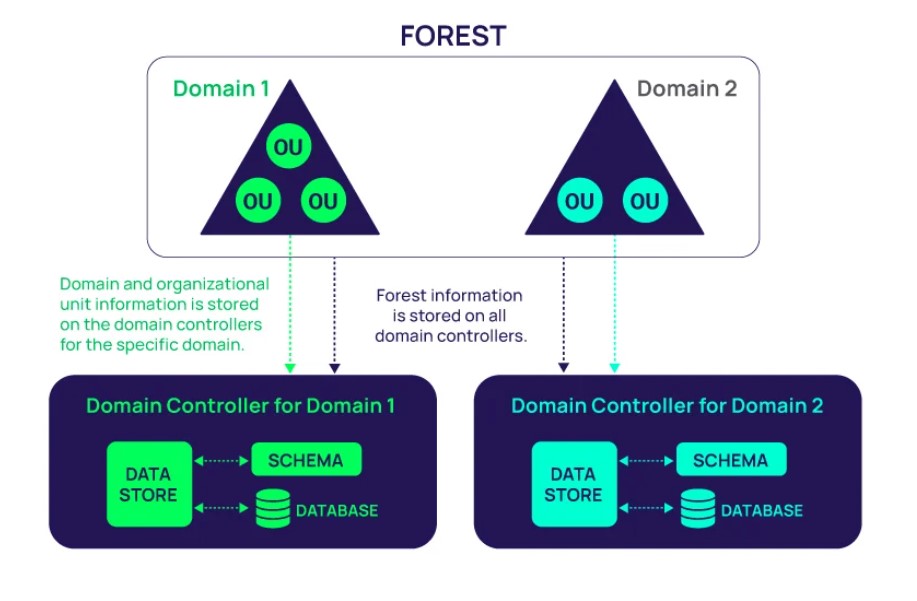
The diagram below illustrates the operational flow of an Active Directory environment with multiple domains in a forest:
🔍 What This Diagram Represents:
Each domain contains its own Organizational Units (OUs), which are logical groupings of users, computers, or groups. These make administration easier by mimicking a company’s real-world structure (like HR, Finance, or IT).
The Domain Controller (DC) for each domain holds:
- A Data Store where actual objects (like users and devices) reside.
- The Schema, which defines the types of objects that can exist and the rules governing them.
- A Database that holds replicated directory data.
All Domain Controllers within a forest share the same schema and configuration data to maintain consistency and interoperability.
Forest-level information (like schema definitions) is replicated across all Domain Controllers, while domain-specific info (like OU structure and user data) remains isolated within each domain.
✅ Why This Matters
- Security isolation between domains
- Administrative delegation through OUs
- Redundancy via domain controller replication
- Scalability to support large, distributed organizations
In real-world terms, this means a company with global branches can have:
- A shared forest for consistency
- Separate domains per country or division
- Independent administration while maintaining trust and replication
👤 Key Concepts You Should Know
🔸 Users
Each person accessing the network is represented by a user object. These accounts come with credentials, roles, and permissions that define what they can and can’t do.
🔸 Groups
Managing individual user permissions can get messy fast. AD solves this with groups:
- Security Groups manage access to resources.
- Distribution Groups manage email distribution lists.
Admins can even nest groups within groups to simplify complex access needs.
🔸 Computers
Every domain-joined device is represented by a computer object in AD. This makes it possible to manage machines as easily as users—with policies, permissions, and monitoring.
🌍 Sites and Global Catalogs: The Backbone of Performance
When organizations span across cities or continents, Active Directory Sites come into play. These map to IP subnets and help AD optimize data replication and direct users to the nearest domain controller.
Meanwhile, Global Catalog Servers store partial replicas of all objects across domains, enabling faster logins and cross-domain searches. Without them, your multi-domain infrastructure would move at a crawl.
🔒 Why Security and Management Matter
Here’s the kicker: Active Directory controls who gets in and what they can do.
If compromised, attackers could gain full control over your systems. That’s why AD management isn’t just an IT task—it’s a cybersecurity imperative.
AD Management Includes:
- Creating and organizing forests, domains, and OUs
- Delegating permissions and access rights
- Monitoring changes and suspicious activity
- Maintaining healthy replication and backups
Tools like Lepide Auditor or Microsoft Defender for Identity allow organizations to track everything from login attempts to permission changes—all in real time.
✅ Benefits of Active Directory
Here’s why companies depend on AD:
| Benefit | Description |
|---|---|
| Centralized Management | One place to manage users, devices, and policies |
| Single Sign-On (SSO) | Login once, access everything |
| Enhanced Security | Fine-grained access control, auditing, and policies |
| Scalability | Grows with your organization |
| Redundancy | Failover and replication for business continuity |